Save the Day With a Simple Declarative Cloud Governance Policy Language
Cloud and security engineering teams are typically very busy managing and securing cloud environments. Suppose a security issue pops up within a cloud platform. In that case, it can be a challenge to write and deploy controls or policies that rectify the issue, while contending with an already busy schedule. Remediation of the issue could even take longer.
For example, if you are a cloud or security engineer, you would typically have to write a lot of custom scripts for each new policy in order to scan or identify where those issues occur within every account and every region you use. Then you would have to deploy these custom scripts to all the accounts and regions to detect at-risk resources. You cannot afford to do this every time.
You need to be able to define policies via a simple, declarative language. In effect, a declarative language teaches what should be done rather than how it should be done. In this way, teams should be able to express any policy their organization requires. Further, employing an understandable, consistent language makes it easier for different groups and individuals to get started, collaborate, and gain alignment on critical objectives and approaches.
Cloud Custodian, an open source cloud governance as code engine, is an excellent example of this approach. Cloud Custodian’s simple YAML policies let you quickly and easily create policies by specifying which resource type to target, what you want to filter within that resource, and what actions you want to take on the filtered resources. Policies can often be authored in just a few minutes and require a fraction of the code that would be needed to script the same thing manually.
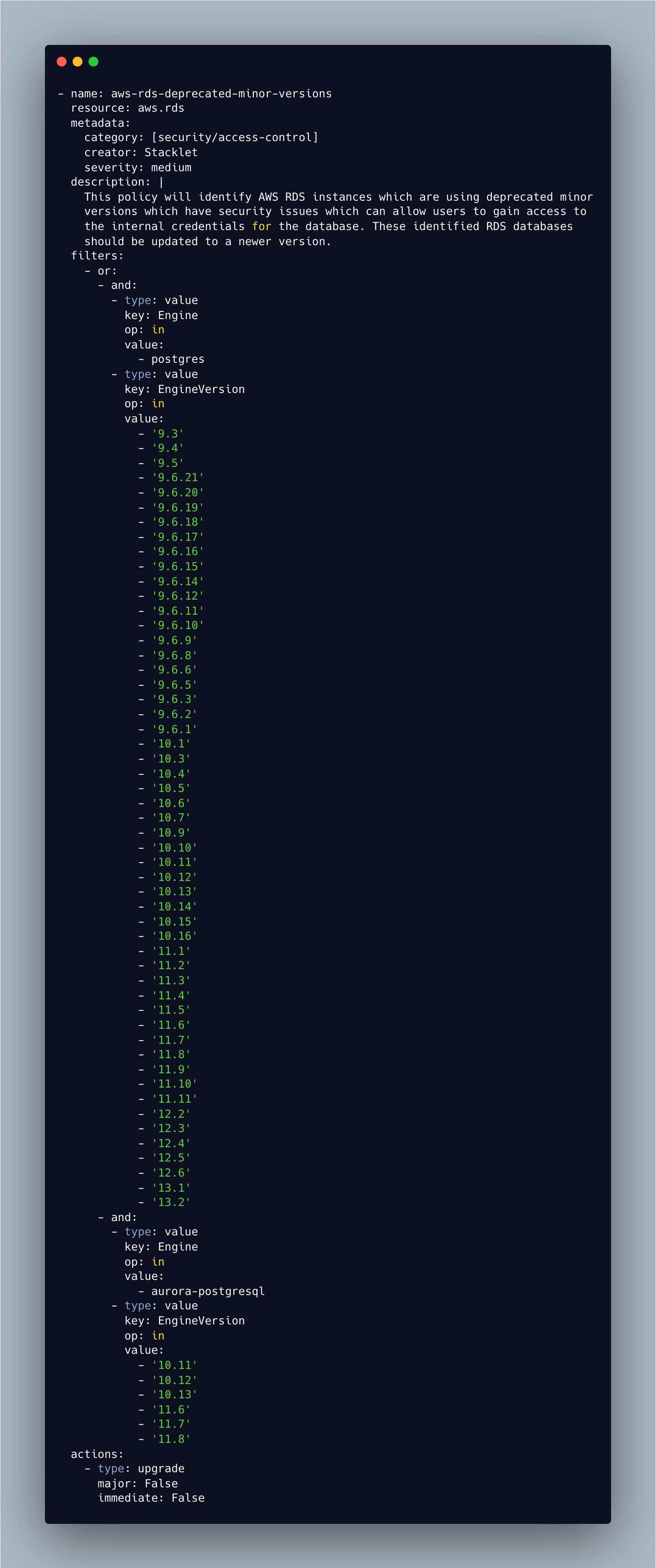
Here’s a case in point: Recently, an issue was reported with Amazon RDS PostgreSQL, resulting in a potential credential leakage. As a result, organizations had to update their RDS databases. I wrote up the Cloud Custodian policy below and deployed it in a few minutes. This policy will identify AWS RDS instances that are using versions with security vulnerabilities. These identified RDS databases should be updated to a newer minor version.
Note action or remediation is part of the Cloud Custodian policy. Similarly, in this policy, the action is built-in; typically to meet your organization’s patching policies, the immediate field should be set to False, which would apply the upgrade during the RDS’s scheduled maintenance window. Applying the upgrade to the databases immediately will cause an unscheduled outage, therefore it is recommended to set the immediate: setting to False.
AWS has a security bulletin page where it posts its security findings and issues. Some of these security issues require customer action to remediate. Subscribing to the page RSS feed is a great way to stay on top of these issues, and you can make sure your environments are compliant using Cloud Custodian policies.
This blog post has been published as part of Cloud Governance Month, which is taking place April 2022. Our goal is to raise awareness about cloud governance. To learn more, be sure to visit our Cloud Governance Month landing page. You can also follow us on Twitter to get regular updates on new tips, resources, and videos available.
Categories
- Cloud Governance Month Content
- Cloud Security