AWS GuardDuty + Stacklet : Turning Cloud Threat Detection into Rapid Action
Cloud threat detection and response is critical to protecting your organization’s data, assets, and reputation. Failing to detect and respond quickly can lead to financial loss, internal disruptions, and reputational damage. Simply put, the faster a threat is detected and remediated, the better.
Amazon Web Services (AWS) has invested heavily in GuardDuty, a service that helps customers detect a wide range of cloud threats. AWS GuardDuty can identify both internal threats, like malware on an EC2 instance, and external threats, such as bad actors scanning for network vulnerabilities.
Stacklet, built by the co-creators of the Cloud Custodian open-source project, delivers a governance as code platform designed to not just detect risks, but to automate remediation and prevention. With Stacklet’s integration with AWS GuardDuty, organizations can quickly act on findings to reduce mean time to remediation, prevent potential breaches, and save valuable team hours that would otherwise be spent manually resolving issues.
In this blog, we’ll explore how AWS GuardDuty findings integrate with Stacklet’s cloud governance as code platform to accelerate and automate threat response.
AWS GuardDuty Overview
AWS GuardDuty provides comprehensive, cloud-native threat detection purpose-built for AWS environments. Developed by AWS security experts, GuardDuty leverages deep knowledge of AWS resources, logging, and metrics to deliver highly specialized threat detection capabilities.
Here’s an overview of the types of threats GuardDuty helps detect. For detailed information, refer to the AWS GuardDuty documentation.
Internal Threats
Internal threats originate from within the customer’s AWS account. These typically result from a compromised resource – such as an EC2 instance infected with malware or accessed by an unauthorized user. Common examples include crypto mining activity, DNS exfiltration, or port scanning originating from the environment.
External Threats
External threats occur when known threat actors attempt to infiltrate AWS resources or scan for vulnerabilities. AWS GuardDuty enriches detections with global threat intelligence, including lists of malicious IPs and known attack patterns. Examples include IAM STS token exfiltration, attacks from known bad actors, and the exposure of S3 bucket vulnerabilities.
Anomaly Detection
When first enabled, AWS GuardDuty builds a baseline profile of your account’s usage patterns, resource behaviors, and network access. Once established, it continuously monitors for deviations from this baseline to flag suspicious anomalies that may indicate a compromise.
Stacklet + AWS GuardDuty: Reduce Time to Remediation and Free Up Staff Hours
Stacklet excels at driving action through multi-step remediation workflows that can be tailored based on the risk profile or nature of the AWS GuardDuty findings. These workflows combine automated notifications with actions on affected resources, reducing both the time to remediation and the manual effort required from engineering teams.
Stacklet also integrates with tools like Jira, ServiceNow, Slack, Microsoft Teams, and others – meeting engineering teams where they work and aligning with your organization’s preferred toolset.
This example workflow achieves the following:
- All Medium and High/Critical findings are logged in Jira to support cloud governance and tracking.
- Resource owners have 24 hours to respond to High/Critical findings before the resource is automatically remediated.
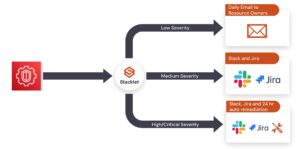
For more details on Remediation Workflows, check out our other blog.
From Findings to Action: Operationalizing GuardDuty with Stacklet Policies
Stacklet policies define how AWS GuardDuty findings are operationalized into action. Policies specify which findings require further investigation, notifications, or automated remediation based on the severity or type of threat.
Stacklet provides a set of out-of-the-box policies for common AWS GuardDuty findings, giving organizations a fast start. These policies are highly expressive and human-readable, making it easy for engineering, security, and governance teams to collaborate on the right actions without needing to decode complex logic.
Workflows can be customized to align with your organization’s specific governance and response standards. For even faster time to value, policies can also be generated using natural language through Stacklet’s Jun0, enabling teams to translate requirements into actionable policies with ease.
As teams build confidence, they can choose to auto-remediate specific threats immediately upon detection, reducing time to remediation while freeing up valuable engineering time.
Below are example Policies which show how Stacklet interprets and processes GuardDuty findings.
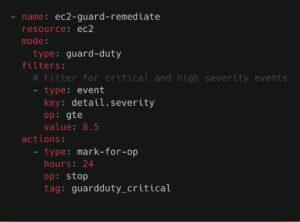
This example policy stops any AWS EC2 instances associated with a High or Critical GuardDuty finding if the issue is not remediated within 24 hours.
When configured with notifications, resource owners are alerted immediately and have 24 hours to remediate the issue in line with company policy.
If the owner does not take action within that window, Stacklet automatically stops the instance to prevent further damage, ensuring threats don’t linger in your environment.
Here is an example of a Policy based on specific GuardDuty findings.

This is an example of a specialized policy designed for a specific AWS GuardDuty finding with a targeted response. In this case, since the instance is almost certainly compromised, the policy will remove the IAM profile, stop the instance, and create a snapshot for investigation.
When paired with a workflow that generates a Jira or ServiceNow ticket, the threat detection team is notified with the full set of forensic details needed for investigation, streamlining both response and analysis.
Conclusion
Protecting your assets and reputation requires more than just detection – it demands rapid remediation and efficient workflows to minimize damage and reduce risk.
AWS GuardDuty delivers powerful threat detection, but detection alone creates a gap between identifying threats and taking action, introducing unnecessary risk and potential delays.
Stacklet completes the equation by providing the workflows, notifications, and remediation capabilities needed to close that gap. With Stacklet, customers can define customized, automated remediation workflows that enforce governance policies while saving valuable team hours.
Over time, organizations can evolve these workflows toward auto-remediation, accelerating time to resolution and reducing the operational burden on threat detection and security teams.
Categories
- Automated Remediation
- Cloud Security