Mastering Cloud Tagging: Key to Effective FinOps, Security, Compliance, and Operations
In the modern, cloud-centric world, cloud tagging has emerged as a pivotal strategy for businesses aiming to streamline their cloud governance and operations. Trying to manage a cloud estate without proper resource tags is like running a big-box store without barcodes on your products: it is simply impossible at scale. Cloud resource tagging is more than just a best practice — it’s a necessity for organizations seeking to maximize their cloud ROI.
Effective tagging is central to FinOps and cost management. By implementing effective cloud tagging strategies, teams can precisely allocate costs, monitor resource consumption, and predict future cloud expenses. However, the benefits of cloud tag management extend beyond finances. On the security front, cloud tags offer a systematic way to identify and safeguard resources, ensuring robust protection and controlled access.
Tagging is indispensable for remediating misconfigurations, whether related to cost or security. With proper tags, teams can efficiently pinpoint the owner of a misconfigured resource, potentially reducing prolonged vulnerabilities or policy violations. In the complex compliance realm, cloud resource tags serve as a structured method to meet stringent regulatory demands, guaranteeing that assets are classified, audited, and reported in accordance with prevailing standards. Cloud tagging stands as a linchpin in optimizing cloud management, merging cost effectiveness with security, compliance, and operational efficiency.
Here are seven keys to getting cloud tagging right:
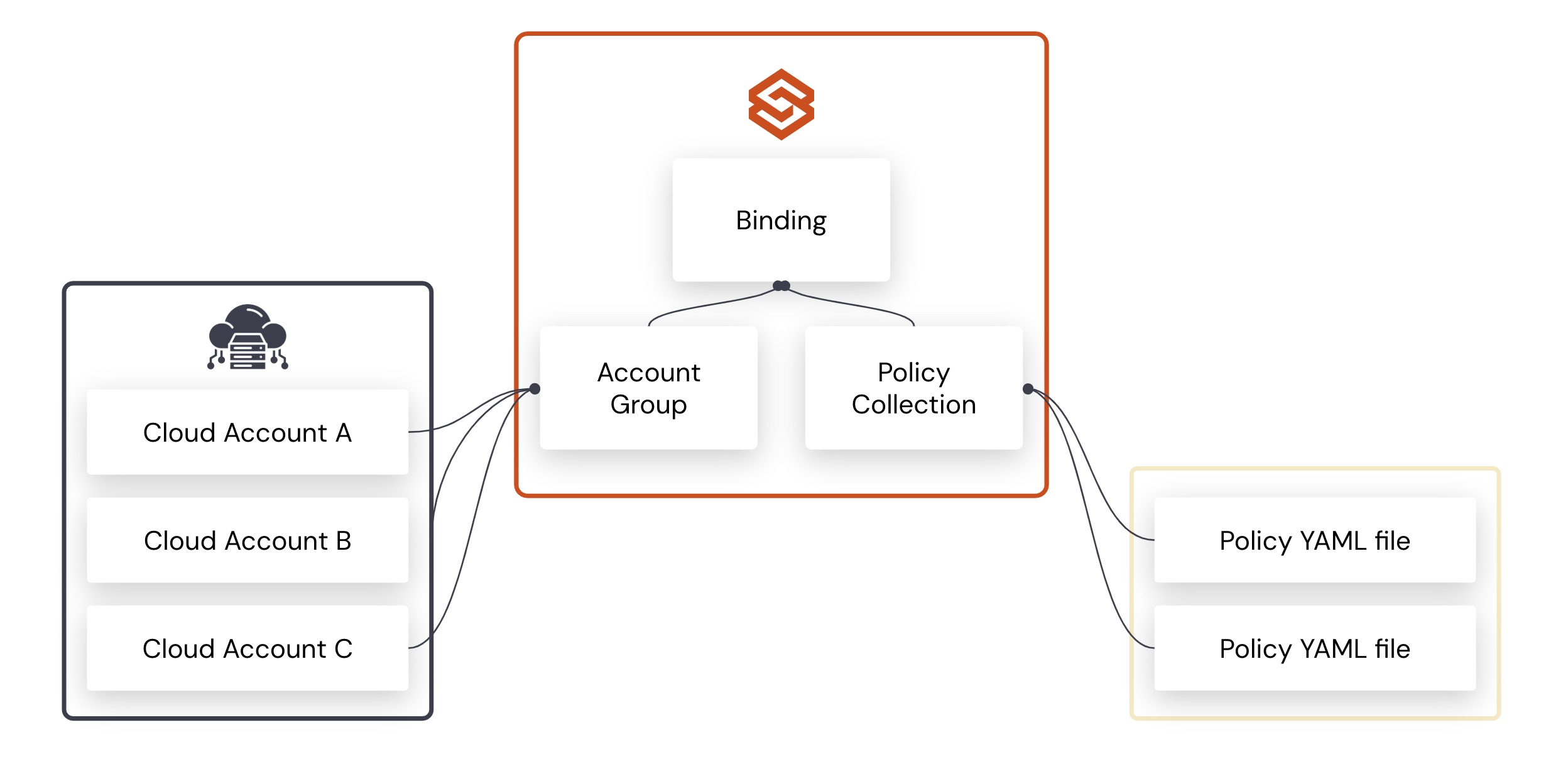
- Start with a small, mandatory set. Typically an organization is going to have a handful of required tags that they need across all accounts and resources. Examples would include resource contact, environment, and business division. Then there’ll be some optional tags that can vary by business unit and resource type. It’s always better to start with the mandatory ones and then address the optional ones.
- Establish, document, and communicate. Organizations should establish, document, and communicate their tagging strategy to all users. This strategy should outline which tag keys the organization requires and what the acceptable values for each tag are. It is also important to outline which resources you are enforcing these tags on and the details of the enforcement process.
- Continuous visibility into existing tagging posture across cloud platforms. Organizations need to take an inventory of all their existing resources, along with their existing tags and owners as they roll out a comprehensive tagging program. This step is essential in finding and starting communications with resource owners. Post roll out, teams would still need this visibility to monitor drifts and adjust their tag posture to meet new business requirements.
- Implement a flexible, automated workflow to fix existing resources. Once you start implementing a particular tagging structure, there will probably be numerous existing resources that need to be “re-tagged.” You might not be able to forcibly remediate tags on existing non-compliant resources. Using flexible policy workflows for existing resources helps alleviate much of the friction. Through this approach, you notify affected users and give them a window to remediate their issues before automatic tag remediation occurs. For example, a policy workflow could identify a resource that is not tagged correctly, and then first send a notification to the associated users. The notification can be sent again on day six if the issue isn’t addressed. On day 12, the policy violation can be escalated to management. This workflow cannot be managed manually, especially for organizations with a significant cloud resource payload. Automation is essential.
- Align the enforcement communication with developer-centric channels. Developers and DevOps teams typically don’t review traditional corporate communication channels like email. Notifications and recommendations of non-compliant resources should be made in channels like Slack or through tickets opened in modern tools like Jira.
- Automate mandatory cloud tag enforcement. For net-new resources, you should apply automatic tags at resource creation to prevent “bad” tags from appearing in the first place. You should be able to add basic tags, such as the user ID of the person who created or modified the resource. These IDs should be based on the user identity drawn from the service used to track real-time events, such as CloudTrail. Automatically tagging the user who last modified a resource can add helpful context and help you track down issues with recent resource changes. In the case of more advanced tags, you might have to automatically notify the resource creator to make the required change.
- Scan and remediate IaC templates for earlier correction of tagging errors. Many organizations are moving towards adopting infrastructure as code (IaC) for provisioning and creating cloud resources. If your organization is using IaC, your team should possess policies and tools that scan IaC artifacts across CI and deployment pipelines, identifying tagging issues early in the cycle. Providing in-line remediation recommendations in tools like Git would help the developer or DevOps engineer correct tags earlier. Plus, fixing the issue in the IaC artifact helps prevent the issue from happening again. However, given your organization probably has multiple ways to provision resources, such as cloud management consoles, you would still need automated tagging, as per the previous suggestion.
Mastering cloud tagging is essential for harnessing the full potential of cloud resources. As cloud environments grow in complexity, our strategies must evolve. By implementing effective cloud tagging, organizations can ensure agility, compliance, and cost effectiveness. Embracing these strategies paves the way for an optimized cloud ecosystem.
Credits: Thanks to Jamison Roberts and Sam Cozannet for providing content and reviewing this blog
Categories
- Cloud Cost Management
- Cloud Governance
- FinOps
- Tagging