Cloud Security Policy Set: Ensure Networks and Cloud Resources Aren’t Exposed

Halloween is right around the corner. It’s an exciting time for kids; they can pick the candy they want, and eat as much as they want. Undoubtedly, that’s the way hackers feel when they see cloud resources or networks publicly exposed. When sensitive assets are exposed, the repercussions can be very costly and harmful to a company’s reputation. That’s why, as part of your cloud security posture management, you need to have policies implemented and continuously enforced. In this way, you can ensure that your sensitive cloud resources or networks are not mistakenly exposed.
In order to secure cloud resources, it is critical to define expected communication paths and identify traffic that falls outside those expectations. For example, if your team only expects applications running on your local network to connect to your database, a connection attempt from a public IP address may be an unnecessary risk.
If a resource is addressable, it can still accept or reject traffic based on port and protocol. For example, a resource running a reverse proxy service may accept inbound HTTP traffic from a wide range of sources but block most SSH traffic. For resources that only accept connections from an internal network, it is important to control the scope of that network. For example, AWS uses features, such as VPC peering connections and transit gateways, to make outside resources part of your local network. Those connections should be verified.
Ideally, these policies should be part of a defense in depth strategy that addresses security concerns in other areas.
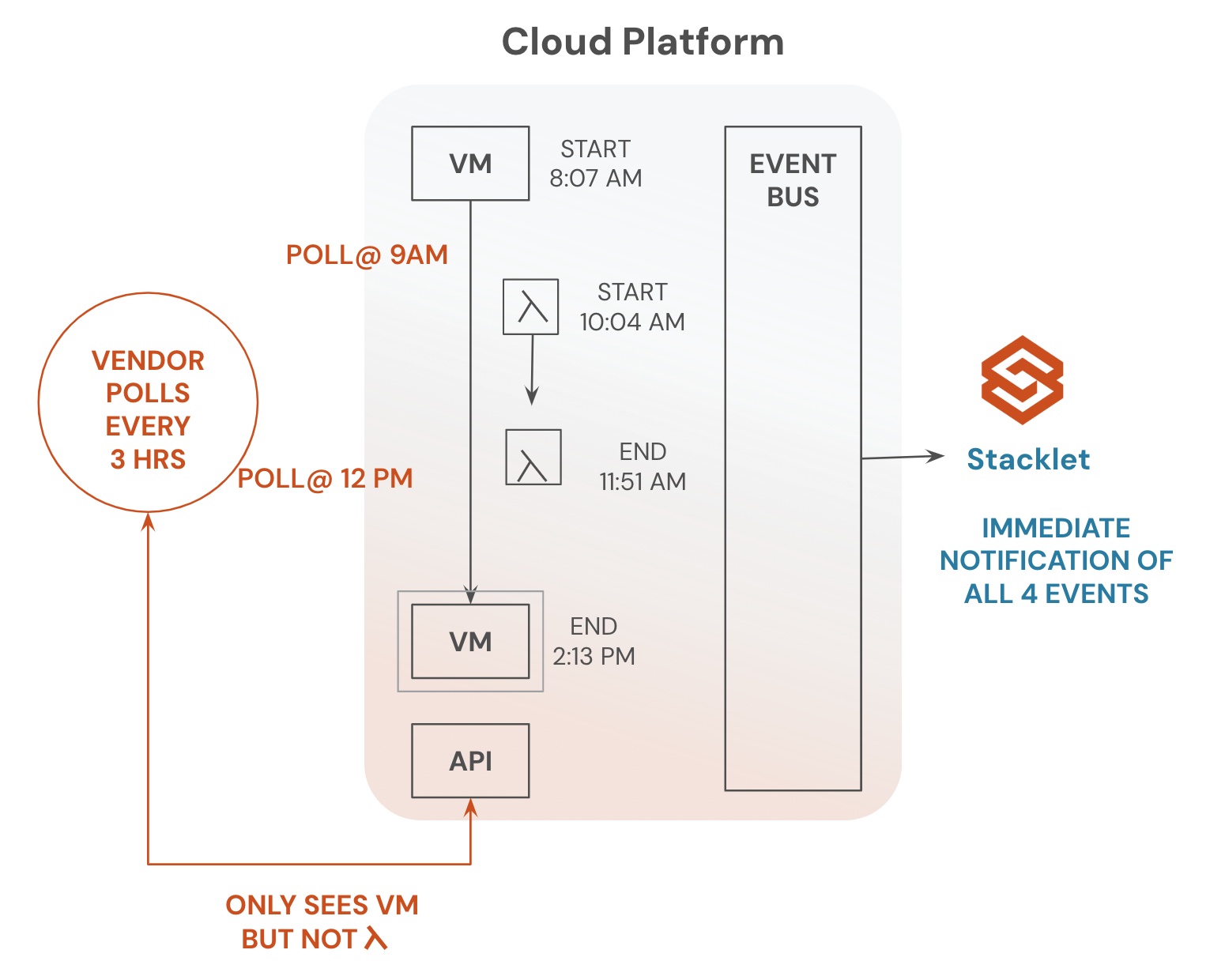
Cloud Custodian is an open source cloud governance and security tool that helps enforce security policies via automated detection, notification, and remediation. You can easily express complex policies in a simple declarative language (YAML) that your development, security, and operations teams can understand. In each policy, you can specify a type of resource to run the policy against, filters to narrow down the set of resources, and actions to take on the filtered set of resources. You can create policies that will help you automatically ensure that your cloud resources and networks are configured correctly
The following example policy will automatically detect and remove security group rules that grant inbound public access. This provides near real-time, automated remediation action—typically within a minute of an erroneous security group change. Automating remediation in this way significantly reduces any attack window. Notifications can also be automated. As a result, the user who tried to perform the action can be informed of the error, which helps improve user behavior on an ongoing basis.
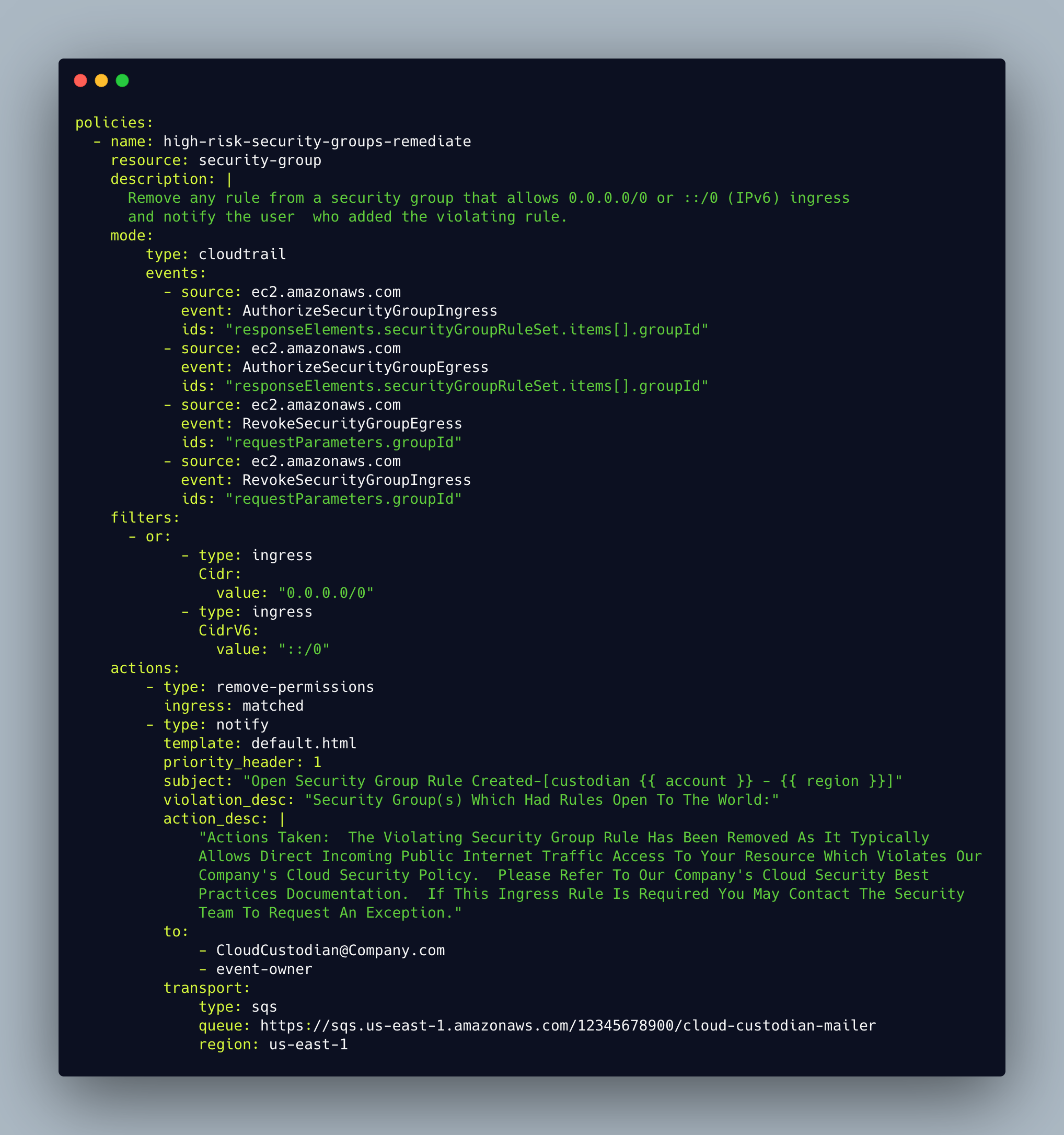
You can find the complete documentation of the policy here. There are additional policies below that you can explore for keeping your cloud resources and networks secure.
- More variations of the same
- Invalid external VPC peering connections
- Microsoft Azure – Block public access to storage
- Microsoft Azure – Public IPs on resources (5 policies)
How do you ensure your cloud resources and network are not exposed? If you can use help, you can start with cloud custodian here.
Categories
- Cloud Security
- Cybersecurity
- Cybersecurity Awareness Month 2021