Cloud Security Policy Set: Enforce Encryption for Critical Cloud Storage and Databases
Just because cloud services may have security controls enabled by default, that doesn’t mean they’re secure. Even if an instance is provisioned with strong controls, Dev or Ops teams might inadvertently alter security configurations as they move applications to production. As part of Cybersecurity Awareness month, we thought we’d share a set of policies (Plus some fun comics) that would make for a more secure cloud. As a bonus, we will be providing links to sample policies that are available in the open source project, Cloud Custodian. Best of all, you can try implementing these policies in your own environment for free.
So let’s move to the first policy: enforcing encryption across your critical cloud resources, such as storage buckets, databases, and more. Encrypting your critical cloud resources ensures that your data is protected and less vulnerable to a breach. It also makes it easier to comply with various compliance and regulatory requirements, such as the General Data Protection Regulation (GDPR).
Some cloud providers have encryption turned on by default. Some don’t. Some provide different options for encryption mechanisms. Resources that are storing confidential information, such as customer or financial data, need to be protected. Organizations need to have security policies that query, check storage and database resources for the existence of sensitive assets, and, when detected, enable the appropriate level of encryption. These policies should be periodically executed or triggered based on a configuration change to avoid any mistakes. Ideally, your policies should include automated remediation actions or workflows specific to the class of data that your storage or database resources host.
Cloud Custodian is an open source project that allows you to enforce cloud governance via code to secure critical resources. Cloud Custodian policies are expressed in YAML and specify a type of resource to run the policy against, filters to narrow down the set of resources, and actions to take on the filtered set of resources.
The following simple policy will enable AWS Key Management Service (AWS KMS) bucket encryption on S3 buckets that don’t have encryption turned on. By using KMS encryption instead of standard AWS AES256 encryption, you are adding an additional layer of security and controls in front of your data. That’s because KMS requires users to have permission granted to the specified KMS key in order to access the data.
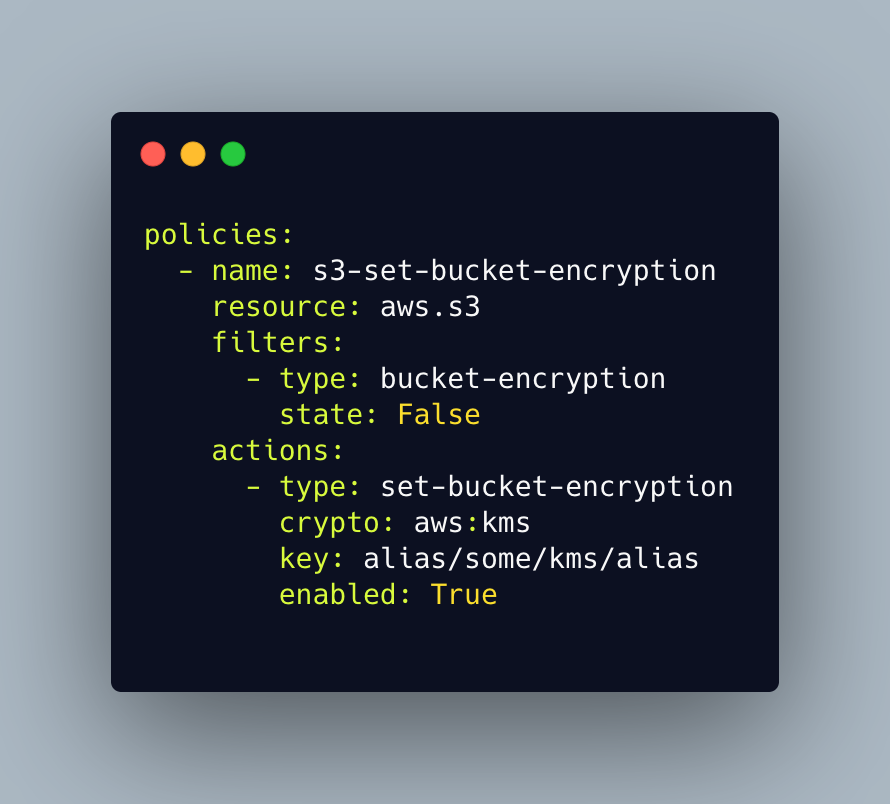
Cloud Custodian can help you scan for non-compliant storage or database resources and remediate them. For example, policies can be enacted to encrypt or de-provision resources or start an escalation notification workflow. Here is the documentation for a few related policies for remediating an un-encrypted resource:
How do you ensure your storage and databases in the cloud are encrypted? If you can use help, you can start with Cloud Custodian here.
Categories
- Cloud Security
- Cybersecurity
- Cybersecurity Awareness Month 2021