Cloud Network Security: Fixing & Preventing Misconfigurations with Stacklet
Cloud network security is critical for protecting cloud environments from cyber threats. Cloud providers must be accessible via the internet to deliver services, but securing network access is essential to maintaining a strong cloud security posture. Unrestricted or misconfigured network connections can expose your environment to attacks, making it crucial to enforce strict controls on both inbound (ingress) and outbound (egress) traffic.
Securing cloud networks isn’t just about blocking external threats – it’s also about monitoring and restricting internal connections. Even if an attacker gains entry, well-architected internal network controls can help contain and mitigate the impact of a breach. Detecting, remediating, and preventing overly permissive network configurations is key to reducing cloud security risks.
Stacklet, created by the same core team behind the Cloud Custodian open-source project, goes beyond traditional security tools by providing policy-driven automation for cloud network security. With built-in policies spanning multiple network services, cloud layers, and providers, Stacklet helps organizations rapidly identify misconfigurations, enforce security best practices, and prevent future risks. This blog will explore how Stacklet’s governance as code platform helps organizations find, remediate, and prevent overly permissive network connections – ensuring a more resilient and secure cloud environment.
Anatomy of a Cloud Network Attack
Direct Attack via Internet Access
This is the most common and obvious way attackers target cloud environments.
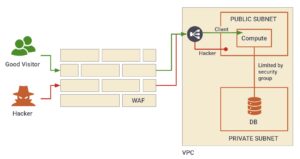
Most cloud users have some public-facing components, such as websites, APIs, or applications, which malicious actors attempt to exploit. In a direct attack, intruders probe well-known ingress points, seeking vulnerabilities to infiltrate your cloud environment while avoiding detection. Any internet-facing entry point becomes a potential target.
Even if there are no public-facing applications, all cloud services rely on API and console access, making cloud administration inherently accessible via the Internet. Without proper controls, attackers can exploit misconfigurations, exposed credentials, or unpatched services to gain unauthorized access.
There are a few ways to prevent these attacks:
- Minimize inbound and outbound internet connections to the absolute essentials – e.g., restricting public access to only HTTPS via a limited set of Load Balancers.
- Ensure microservices within containers are not publicly accessible unless explicitly required.
- Apply Stacklet policies to continuously detect and remediate exposed network endpoints, ensuring misconfigurations are promptly addressed.
- Audit network logs for unusual connections and unauthorized access attempts.
Detecting and Remediating Ingress Points with Stacklet
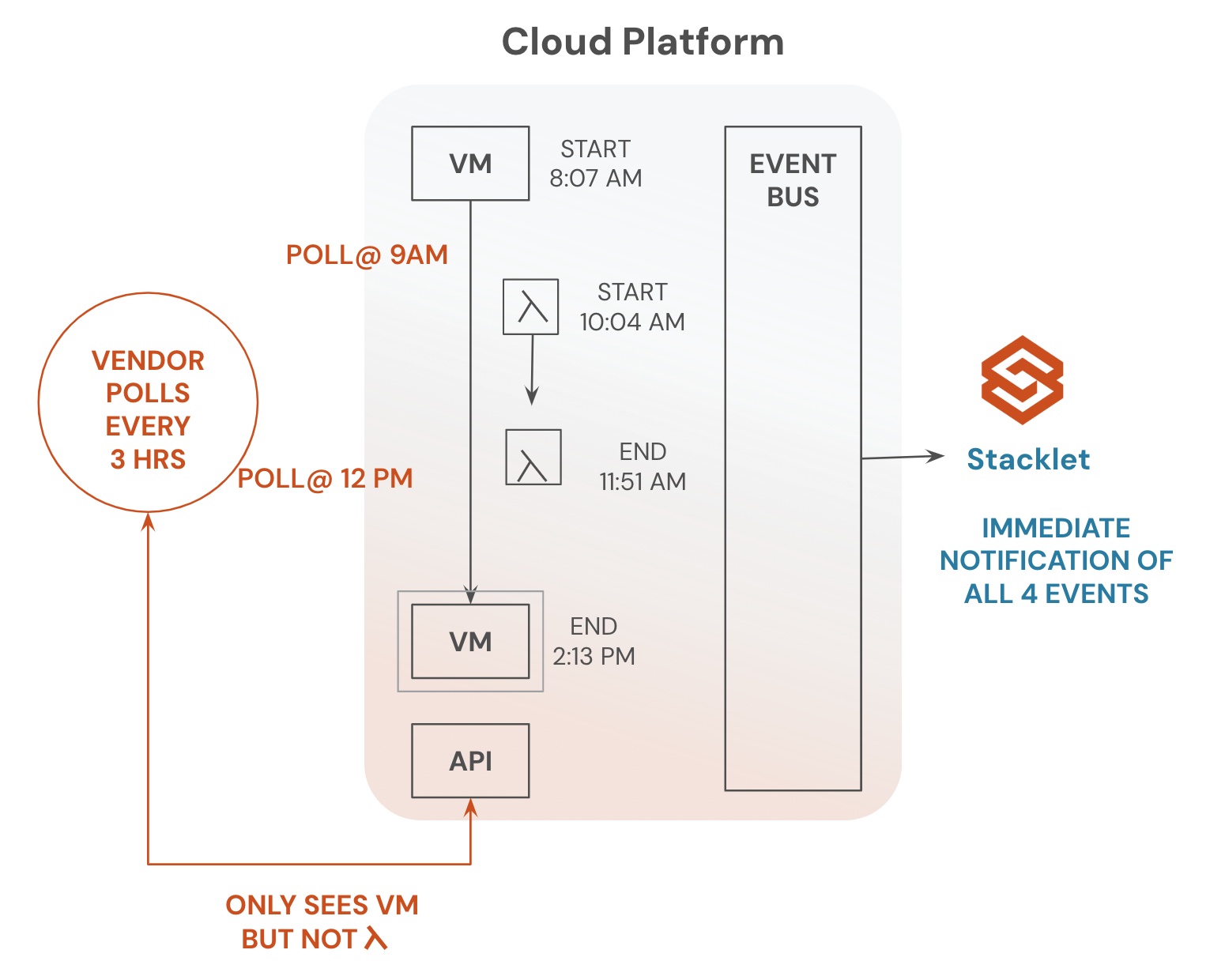
Manually tracking all ingress points in your cloud environment is nearly impossible – especially in dynamic, auto-scaling environments where Public IPs frequently change. Without the right tooling, blind spots emerge, increasing the risk of unauthorized access and security vulnerabilities.
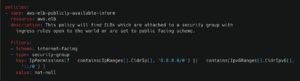
Stacklet provides prebuilt policies – and the flexibility to create custom workflows – to monitor, detect, and take action on incoming network traffic across major cloud providers. Below are foundational ingress policies for key cloud platforms that can be customized to enhance your organization’s cloud security posture and enforce proactive network protection.

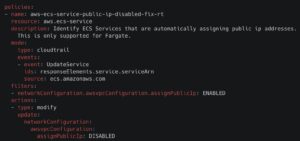
Containing Cloud Attacks: Preventing Lateral Movement with Stacklet
If an attacker gains access to your cloud environment, their next step is typically to scan for sensitive data, move laterally across resources, or even launch a ransomware attack. Without proper containment measures, an initial breach can quickly escalate into a full-scale compromise.
Containment strategies help limit the attacker’s ability to move within your cloud environment by restricting unnecessary network connectivity. For example, if an EC2 instance does not require Secure Shell (SSH) access, it should not allow ingress on port 22, which is the default SSH port. By enforcing strict internal network controls, organizations can significantly reduce their attack surface.
The best way to contain an attack is to continuously review and minimize internal network connectivity between resources within your cloud environment. Enforcing least privilege network access ensures that only necessary connections are permitted, preventing attackers from easily spreading within your infrastructure.
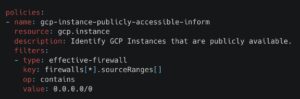
Below are Stacklet policies that help restrict internal access within cloud environments. These policies target well-known ports (e.g., 22 for SSH) but can be easily customized to match your organization’s specific security requirements.
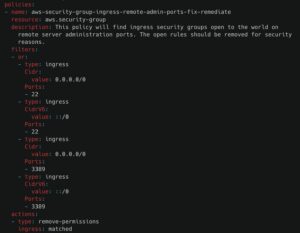
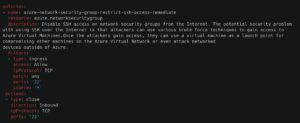

Mitigating Denial of Service (DoS) Attacks in the Cloud
A Denial of Service (DoS) attack occurs when an attacker overwhelms a cloud environment with excessive requests, preventing legitimate users from accessing your application. When this attack is executed from multiple
Without proper mitigation, these attacks can have two major consequences:
- Frustrated customers due to slow or unavailable applications.
- Increased cloud costs as auto-scaling infrastructure struggles to handle the surge in requests.
Unlike direct attacks, where an attacker attempts to gain unauthorized access, a DoS/DDoS attack is purely disruptive, designed to consume resources and degrade service availability. Fortunately, cloud providers offer Web Application Firewalls (WAFs) and dedicated DDoS protection services to mitigate these threats.
Manually ensuring that all Application Load Balancers have WAF protection enabled is time-consuming and error-prone. Without tooling, misconfigurations occur, leaving applications vulnerable to DoS attacks. Stacklet provides prebuilt policies that continuously detect and enforce WAF configurations across AWS, Azure, and GCP – ensuring your cloud applications remain protected from DoS and DDoS threats.
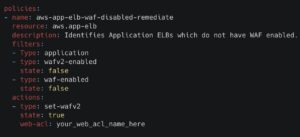
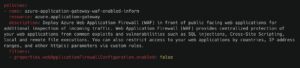
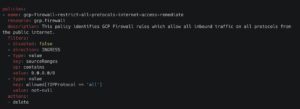
Adapting Cloud Network Security Policies
The examples above demonstrate how Stacklet policies leverage a simple Domain-Specific Language (DSL) to abstract away cloud provider complexities. This allows engineers to focus on enforcing security controls without needing deep knowledge of provider-specific configurations.
No cloud governance tool can anticipate and enforce network security for all customers. Instead, organizations should start with a strong set of baseline policies and customize them to fit their unique network architecture.
For example, organizations may need to enforce specific egress (outbound) controls to prevent unauthorized data exfiltration. If an EC2 instance should only communicate via HTTPS within a VPC, a custom egress policy can be created to restrict outbound traffic accordingly.
Beyond adapting policies for business-specific security requirements, organizations must also ensure that network security aligns with industry compliance frameworks such as CIS, NIST, SOC 2, and PCI DSS. Stacklet enables automated compliance guardrails, helping organizations enforce best practices while meeting regulatory standards – without the burden of manual audits or ongoing policy maintenance.
Conclusion
Network security is a critical pillar of cloud security. However, securing cloud networks is challenging due to their multi-layered architecture and constantly changing nature – with resources dynamically scaling, shifting, and interacting across environments. Given these complexities, organizations must proactively monitor and enforce security controls on all network-connected resources.
Stacklet Platform provides an automated, scalable solution to detect and remediate network misconfigurations across thousands of cloud resources. With event-driven, real-time enforcement, Stacklet ensures that misconfigurations, public exposures, and security risks are identified and resolved immediately – preventing vulnerabilities from persisting in the cloud environment.
With flexible, policy-driven enforcement, organizations can establish baseline security policies and adapt them to their specific network needs, while also ensuring continuous compliance with security standards like CIS, NIST, and SOC 2.
By leveraging Stacklet’s governance as code approach, organizations can continuously enforce their network security architecture, prevent vulnerabilities, and automatically remediate risks as they arise – ensuring a secure, compliant, and resilient cloud environment.
Categories
- cloud compliance
- Cloud Security