The road to adopting cloud compliance benchmarks at scale
In cloud compliance, organizations look to adhere to various public regulations and benchmarks, such as Critical Security Controls(CIS), the Health Insurance Portability and Accountability Act (HIPAA), and the NIST Cybersecurity Framework. These standards can help support a range of objectives, including effective auditing to ensure security, alignment with industry best practices, and enhanced implementation maturity. When the imperative for organizational improvement arrives, cloud and security practitioners have a series of steps to take, which have an impact on many aspects of software development and cloud deployment processes.
To start, teams must identify which aspects of the benchmark apply to their use of the cloud. They must also determine how their development, CI/CD, and observability tools and capabilities need to evolve. Then they must do internal audits and remediate any cloud infrastructure uses that fall short of best practices or compliance mandates. Here are a few key steps to making this happen:
Establish Holistic Cloud Estate Visibility
Many teams only have limited visibility into their cloud estate. Larger organizations tend to have projects that run across multiple deployment regions, use hundreds of accounts, and span numerous cloud providers. Teams often use multiple tools that offer only piecemeal visibility and increase operational overhead. Without clear visibility, governance of the cloud estate simply isn’t possible. Constructing a complete and accurate picture of your cloud estate is an essential first step before taking on policy enforcement.
Ensure Uniform and Ubiquitous Tagging of Accounts and Resources
Today, larger organizations often have geographically dispersed teams contributing to projects and consuming resources. Further, teams may be using many accounts across many lines of business. Given this, meeting even basic requirements, such as ensuring S3 buckets are consistently configured and compliant, can prove challenging. If good governance is like climbing a mountain, an effective tagging program is the first l toehold. Teams can map resources, even ephemeral ones, to their respective stakeholders through effective tagging. They can also readily identify which environments (staging or production, for example) and applications these resources serve.
Deploy and Enforce Policies at Deployment
When beginning to enforce policies, teams can use various techniques. For example, they can move all teams to a single CI/CD pipeline with some automatic policy enforcement. They can also try to enforce policies through issuing executive mandates, restricting access to specific forms of provisioning, or implementing process changes. These approaches can provide an initial baseline for governance, but they tend to be difficult to enforce and degrade over time. For example, teams will typically have a variety of ways to provision new cloud resources, including through experimentation on the command line or the cloud providers’ console. In these cases, it is unlikely that these resources will be properly tracked, tagged, or kept up to date in an ever-evolving threat and risk landscape.
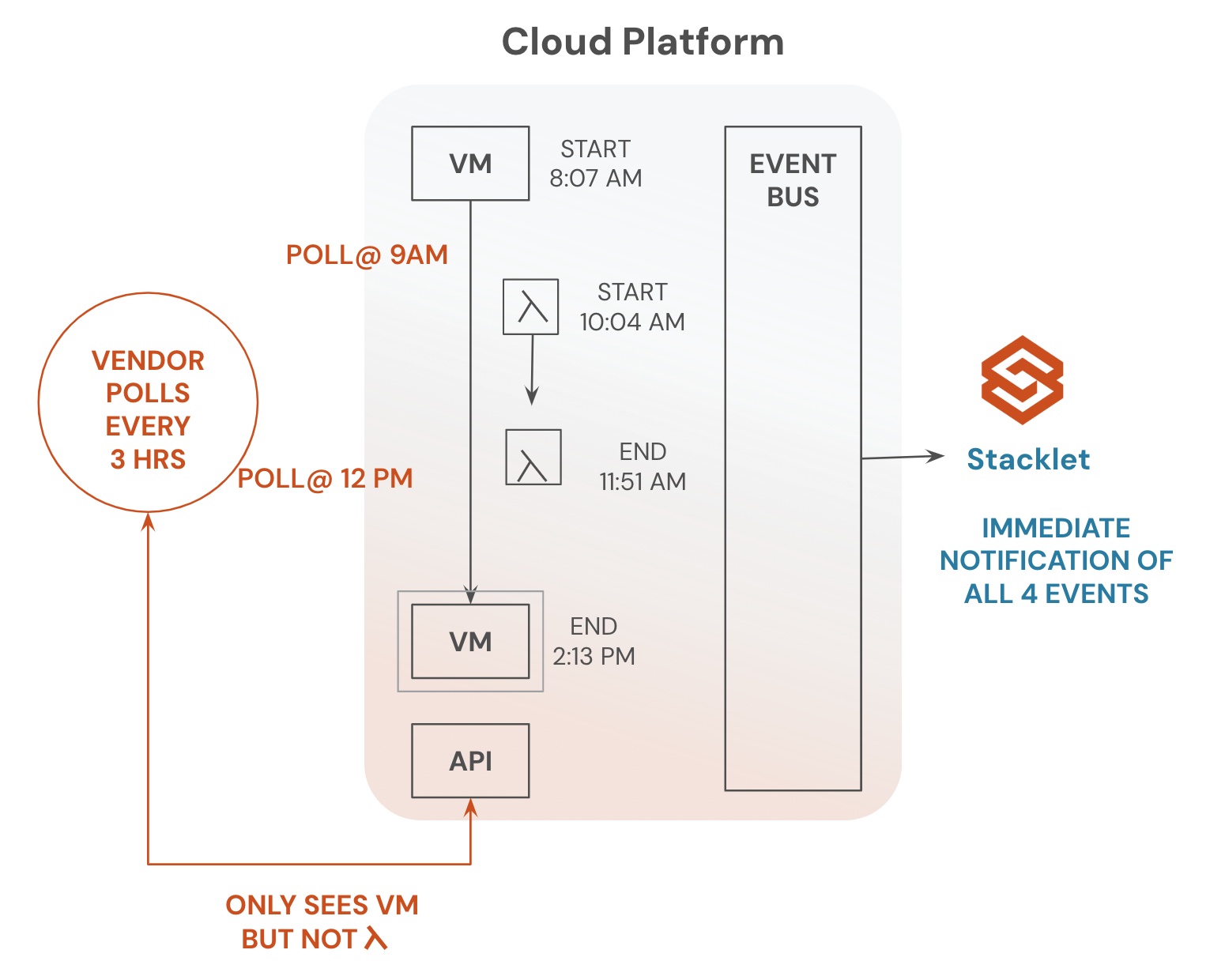
Real-Time Identification of Changes
While process and tooling improvements at the deployment stage are essential, it is even more critical to establish capabilities for monitoring compliance status and for reacting quickly when changes occur. This is particularly true given the challenges outlined above. Teams need to have comprehensive visibility into the status of their compliance posture and use that visibility to drive behavior change. Products in this space tend to specialize in providing some reporting relative to a specific standard and offer varying levels of multi-cloud support. These offerings can typically provide some level of observability and, in many cases, suggest improvements that could help remediate violations.
Automate Policy Enforcement for Scale
When the identification of compliance issues is coupled with the ability to notify stakeholders and perform automated, programmatic remediations, the problems associated with governance at scale become much more manageable. This is a challenge as most products don’t provide any way to automate remediations, workflows, or escalations. This is complex for many reasons:
- First, remediations need to be well understood and effective or they will introduce significant risk to critical systems.
- Second, while the old-school version of “1000 bash scripts” that run in the enterprise is still possible, it doesn’t scale well across teams and is difficult to understand. Each new script attempting to automatically remediate some class of issues becomes an additional source of risk due to implementation variance.
- Third, scripts of this nature are rarely triggered by events from the cloud infrastructure directly. As a result, these approaches are subject to the problems of polling, which can range from latency issues to being susceptible to hitting cloud rate limits and inadvertently impacting other services.
Introducing Cloud Custodian
Cloud Custodian has become the lingua franca for expressing cloud governance as code for many cloud practitioners. Cloud Custodian provides a ready mechanism for responding to infrastructure changes, enabling teams to choose from a suite of actions, including notifications, tagging, and more sophisticated remediations such as an escalation workflow that ultimately results in the deletion of a non-compliant resource. The solution offers the entire cloud estate visibility, including those that span multiple cloud provider environments. It also provides integrations with external notification, ticketing, and workflow systems. All these capabilities make it much easier to reach the peak of effective cloud governance.
At Stacklet, we offer a SaaS platform that makes it easier to adopt, maintain, and scale Cloud Custodian across multiple clouds and organizational groups. With the solution, you can get started in minutes and realize immediate value. It enables you to gain an operational overview of your multi-cloud estate. Plus, you can customize our compliance products to fit your particular needs.
This blog post has been published as part of Cloud Governance Month, which is taking place in April 2022. Throughout the month, our goal is to raise awareness about cloud governance. We’ll be delivering a range of tips and resources, and we’ll be organizing a number of virtual events. To learn more, be sure to visit our Cloud Governance Month landing page. You can also follow us on Twitter to get regular updates on new tips, resources, and videos available.
Categories
- cloud compliance
- Cloud Governance Month Content