Real-World Guide to Automating Remediation Workflows in the Cloud
Cloud offers immense potential for scalability, flexibility, and innovation. However, governing the cloud introduces many challenges, particularly ensuring it’s cost-optimized, secure, compliant, and adheres to industry benchmarks. Traditional manual remediation processes, while once effective, are no longer feasible in the vast and dynamic expanse of the cloud. These processes are time-consuming, costly, and prone to human error, making them unsustainable for cloud-scale operations. Moreover, the prevalent skills shortage exacerbates these challenges, as engineering teams often need more domain-specific knowledge in security, compliance, and financial operations for effective remediation. This gap leaves organizations vulnerable to risks that can significantly impact their financial health, security posture, and regulatory compliance.
- Cost Optimization: Without a proactive approach to cost optimization, opportunities to reduce waste and optimize usage can be overlooked, and costly misconfigurations can persist undetected. These oversights not only inflate the cloud bill unnecessarily but also divert valuable financial resources that could be better invested in innovation and growth. Automated remediation workflows can help identify and correct cost inefficiencies rapidly, ensuring that organizations only pay for what they genuinely need and maximizing their return on cloud investments.
- Security: Vulnerabilities and risky configurations, if not addressed promptly, can expose organizations to significant risks, including data breaches and system intrusions. The consequences of such security incidents are severe, ranging from financial losses to irreparable damage to an organization’s reputation. Automating the remediation of security issues is critical to maintaining a robust defense posture, enabling real-time detection and correction of vulnerabilities before they can be exploited.
- Compliance: Navigating the maze of regulatory requirements and industry standards is daunting in the cloud. Non-compliance can result in hefty financial penalties and legal repercussions, undermining an organization’s credibility and trustworthiness. Automated compliance checks and remediation processes ensure that organizations continuously align with these standards, mitigating risks and reinforcing their commitment to security and privacy.
Automating remediation workflows enhances security, optimizes costs, and significantly boosts engineer productivity. By establishing consistent and predictable workflows, automation reduces the manual burden on technical teams, allowing them to focus on innovation rather than routine maintenance. This shift accelerates development cycles and improves job satisfaction by freeing engineers from the repetitive tasks associated with manual remediation efforts.
However, automating remediation workflows presents challenges, including managing exceptions, accommodating stakeholders, addressing the diverse risk profiles of varying workloads, and adapting to the skill levels of different teams. To navigate these complexities effectively, here are some best practices:
- Communicate Rollouts in Advance: FinOps and DevSecOps teams, depending on the policy type, must ensure that policies for automated remediation workflows and their deployment schedules are communicated clearly and widely within the organization. These communications should detail each policy’s deployment specifics, including its scope and target areas, and explain the rationale behind its implementation – whether it’s for cost optimization or compliance with industry standards. By planning and announcing these policies well in advance, organizations can reduce friction and minimize any potential disruptions to their teams.
- Stagger Remediation Gradually with Selective Policy Implementation: When rolling out auto-remediation policies, it’s crucial to not only phase the deployment across environments but also to be selective about the types of policies you implement initially. Start by deploying these policies to test and refine them safely in development environments. Before introducing these policies to production, utilize “notify-only” policies to familiarize teams with potential issues, aiming to educate rather than enforce them. This step is essential to acclimate teams to auto-remediation gradually without immediate enforcement. Additionally, avoid deploying all types of auto-remediation policies at once. Select a few key policies that address the most critical or common issues as your starting point. This careful, iterative approach prevents overwhelming teams with too many changes simultaneously. It allows for adjustments based on feedback and observed outcomes, leading to a smoother, more manageable transition to full-scale auto-remediation.
- Manage Exceptions with Care: It’s crucial to acknowledge that specific applications or workloads may require exceptions from automated remediation processes due to specific business needs, such as an S3 bucket intentionally left open for hosting public images or websites. However, improperly managed exceptions can lead to engineering teams’ resistance and undermine automation efforts’ credibility. To avoid this, it’s essential to implement a robust process for granting, managing, and regularly reviewing exceptions, ensuring they are handled efficiently and maintaining the overall security and efficiency of the organization.
- Implement Multi-Step Remediation Workflows for Real-World Scenarios: The concept of automated remediation often conjures images of instant, decisive action on compromised resources. While immediate action is appropriate for certain high-risk scenarios, like severe security misconfigurations, real-world scenarios frequently demand more nuanced, multi-step workflows. These begin with initial notifications or warnings, allowing time for assessment and, depending on the severity and context, eventual intervention by automated tools or manual action from engineers. This approach ensures that remediation measures are tailored to the specific needs of each scenario, balancing swift action with thoughtful analysis.
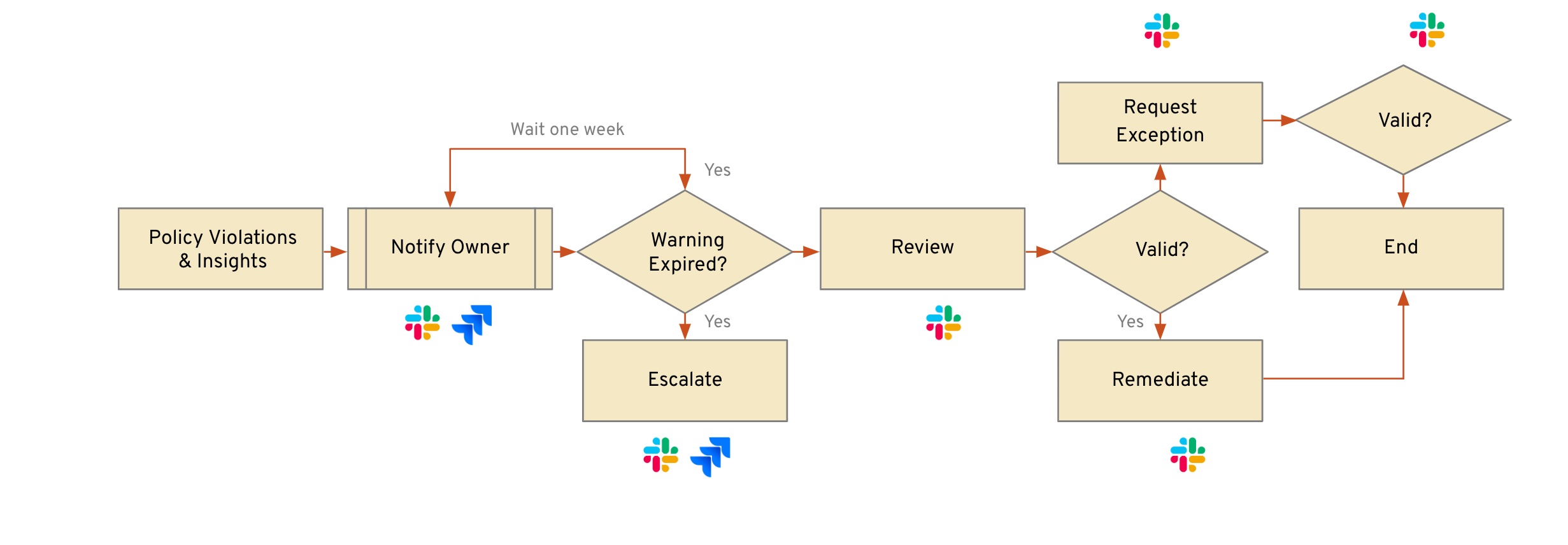
- Employ automation with notifications, actions, and workflows: To improve engineers’ productivity and minimize risks, errors, or disruptions across environments, it’s vital to eliminate manual steps, multi-tool processes, and reliance on ad-hoc scripts. Aim to automate the entire lifecycle of remediation workflows, starting with notifications of issues to the right owners and recommended actions. Escalations should also be automated, integrating seamlessly with your ticketing systems, email, and messaging platforms to ensure timely reminders and follow-ups. An example workflow might automate the detection and notification of a misconfigured resource and propose one-click remediation actions or streamlined processes for requesting exceptions, significantly easing the workload on engineers responsible for maintaining these resources.
- Communicate During Remediation: Effective communication is crucial when initiating auto-remediation workflows or taking corrective actions. It’s essential to keep the account owner or the relevant engineering lead informed at every process step. Share detailed information on the actions taken and the underlying company policies guiding these actions, and, if possible, include a link to the policy repository. This approach not only educates team members about best practices and company standards but also encourages positive behavior and helps to minimize future deviations. Precise, continuous communication fosters a culture of transparency.
- Integrate Remediation Workflows into Developer-Centric Processes and Tools: In many organizations, the responsibility for executing or approving remediation actions falls on cloud engineering, DevOps, or SRE teams. To streamline this process, it’s crucial to embed organization policies, remediation notifications, actions, and recommendations directly into the workflows these teams already use, such as CI/CD pipelines. Additionally, communicating these elements through preferred channels like Jira and Slack ensures that remediation becomes a seamless part of daily operations, enhancing efficiency and compliance without disrupting the development cycle.
- Measure Success and Celebrate Achievements: Effectively tracking and highlighting the outcomes of remediation actions, automated or manual, is crucial. Beyond mere tracking, quantifying the business impact – such as estimated cloud cost savings, mitigated risks, and compliance standards met – demonstrates the tangible value of your remediation efforts. Sharing these accomplishments validates the effectiveness of the strategies employed and motivates and recognizes your team’s hard work. Celebrating these milestones fosters a culture of recognition and continuous improvement, which is essential for maintaining momentum and morale in the face of ongoing operational challenges.
By embracing these strategies, organizations can confidently navigate the complexities of the cloud, ensuring their infrastructure is resilient, secure, and cost-effective. As we look to the future, continuous improvement and adaptation of these practices will play a pivotal role in cloud operations’ success, efficiency, and sustainability. Let’s commit to a proactive approach to remediation, where innovation, security, and efficiency converge to drive our digital world forward.
Credits: Thanks to Kapil Thangavelu and Jamison Roberts for providing content and reviewing this blog
Categories
- Automated Remediation
- Cloud Cost Management
- Cloud Governance
- FinOps