Automated, Tailored Governance with Hierarchical Policies for Cloud Environments
Cloud adoption has accelerated across organizations, bringing significant gains in productivity and speed. As more teams move workloads to the cloud, the complexity of managing security, compliance, and cost grows exponentially. Cloud governance and continuous optimization becomes harder to sustain and scale, and enforcing consistent guardrails across diverse environments becomes increasingly difficult.
Teams across FinOps, security, compliance, and operations all have different objectives. Risk profiles vary by environment and business unit – development teams need flexibility and cost awareness, while production workloads demand stricter controls and full compliance. Applying a single set of static policies manually across all environments often results in unnecessary friction, or enforcement gaps.
Why Automated, Layered Governance Matters
As cloud environments grow, organizations need a governance model that enables automated, tailored policy enforcement. This means applying universal baseline controls – such as encryption, tagging, and usage policies – across all accounts, while layering on environment-specific rules where needed.
For example, all S3 buckets may require some level of encryption by default. In production, that baseline can be extended to enforce stricter standards like AWS KMS with customer-managed keys to meet compliance requirements such as HIPAA or SOC 2.
The same approach applies to FinOps. Development accounts may include policies that automatically shut down unused or oversized EC2 and RDS resources during nights and weekends to reduce waste. By contrast production policies may focus on monitoring for underutilization while ensuring critical resources remain available.
By layering governance in this way, organizations can align policy enforcement with real-world needs – balancing security, compliance, and cost efficiency without increasing manual overhead.
Hierarchical Policies: A Core Building Block for Efficient, Scalable Cloud Governance
Hierarchical Policies provide a structured approach to enforcing cloud governance efficiently across complex environments. Organizations can define a baseline layer of policies that apply to all accounts – such as encryption or tagging – and add additional layers based on the needs of specific teams, environments, or risk profiles.
This approach allows governance to adapt to business needs and operational requirements without duplicating or managing separate sets of policies. The benefits include:
- Faster adoption across teams, as policies are easier to understand and manage.
- Greater scalability, since new accounts and environments automatically inherit the right controls.
- Improved consistency, visibility, and operational efficiency, with flexibility built in.
Hierarchical policies also encourage cross-functional collaboration. FinOps, security, and cloud operations teams can define and manage their own policy layers while staying aligned within a shared governance framework.
This layered, modular model is essential for any organization that wants to scale cloud governance without slowing down innovation or increasing operational overhead.

Hierarchical Policies with Stacklet
In Stacklet, built by the creators and lead maintainers of CNCF’s Cloud Custodian project, hierarchical policies provide a structured, modular way to apply baseline governance across all accounts, while layering on more specific controls for different teams, environments, or compliance needs.
Before diving into how these policy layers come together, it’s helpful to understand three core Stacklet capabilities that make this possible:
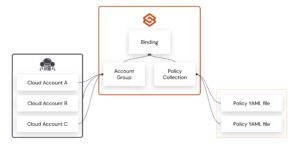
- Policy Collections: define the actual governance rules applied to account groups. These can include policies related to cost optimization (FinOps), security, compliance, and operations. Policies are written in a human-readable YAML format, making them easy to understand, maintain, and scale.
- Dynamic Account Groups (DAGs): that automatically organize accounts based on name, organizational unit (OU), or tags. When a new account is created, Stacklet applies these rules to assign the account to the appropriate group automatically. An account can belong to multiple DAGs, which means it can inherit multiple Policy Collections. This flexibility enables tailored governance across overlapping dimensions, such as environment (e.g., Dev vs. Prod) or business unit.
- Bindings: connect policy Collections to dynamic account groups, enabling automated enforcement. For example, a baseline policy collection can be bound to a DAG that includes all accounts, ensuring consistent governance across the organization. Additional Bindings can apply more specific policies to groups like Development or Production. This is how Stacklet enables layered governance: baseline policies apply to all accounts, while environment-specific layers are added on top based on DAG membership.
Putting It All Together: Building Hierarchical Policies in Stacklet
The simplest way to implement hierarchical governance in Stacklet is by starting with a baseline policy collection. This is a set of foundational policies – such as encryption enforcement or limiting public access to storage—that apply across all accounts. You can bind this policy collection to a dynamic account group that includes every account in your organization.
Even though this setup is simple, it’s highly effective. A baseline policy collection can help ensure critical controls are in place everywhere – for example, verifying that all AWS RDS instances are encrypted or that no S3 buckets are publicly accessible.
From there, you can extend governance by creating additional dynamic account groups, such as one for Development and another for Production. Each group can have its own Policy Collection with rules tailored to its specific needs. For example, development accounts might include cost-optimization policies, while production accounts enforce stricter compliance and availability requirements.
This layered structure is what enables hierarchical policies in Stacklet. It gives teams the flexibility to define and enforce policies at multiple levels – without conflict, duplication, or manual overhead.
Layered Policy: Simple Additive Use Case
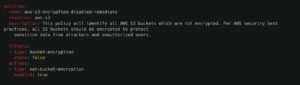
For example, let’s assume the universal baseline policy collection includes a policy that ensures S3 buckets have encryption enabled:
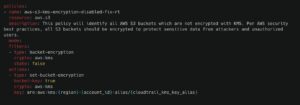
However, for production accounts that must meet compliance standards such as HIPAA or SOC 2, default encryption may not be sufficient. These environments may require stricter controls, such as enforcing KMS-based encryption using customer-managed keys:
This additive approach allows baseline controls to be applied consistently, while enabling tighter policies to be layered on top where needed.
Layered Policy: Use of Exception Lists
Another common use case involves adding policy layers with exceptions for specific resources or scenarios. These are helpful when certain accounts or workloads require a different treatment due to licensing models, cost, or other operational reasons.
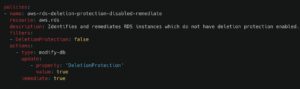
For example, let’s say the organization has a baseline policy ensuring that all RDS instances have Delete Protection enabled to prevent accidental data loss:
However, in a few select accounts, the organization may run specialized (and expensive) Oracle RDS instances under a Bring Your Own License (BYOL) model. These resources must be tracked carefully to avoid violating licensing terms.
In this case, you might use a policy that automatically deletes any unauthorized Oracle BYOL instances not on an approved exception list:
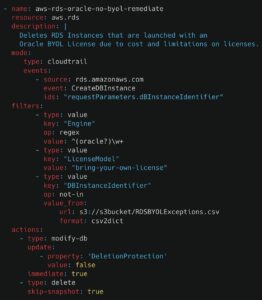
And the CSV file referenced above might look like:
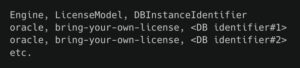
With this layered model, baseline protections are always enforced, while exceptions and edge cases are handled precisely and automatically.
With Stacklet, organizations can implement hierarchical policies that are both flexible and automated – ensuring the right level of governance is applied where and when it’s needed. This approach helps resolve friction between teams, supports different enforcement needs across environments like Dev and Prod, and gives you the foundational structure to scale usage with confidence, control, and efficiency.
Categories
- Cloud Governance
- cloud-custodian


